Social Signals
Phishing scam targets Microsoft Ad accounts via Google Search
Cybercriminals are exploiting Google Search ads to steal Microsoft advertising account credentials, revealing a sophisticated phishing scheme that has potentially been active for years.
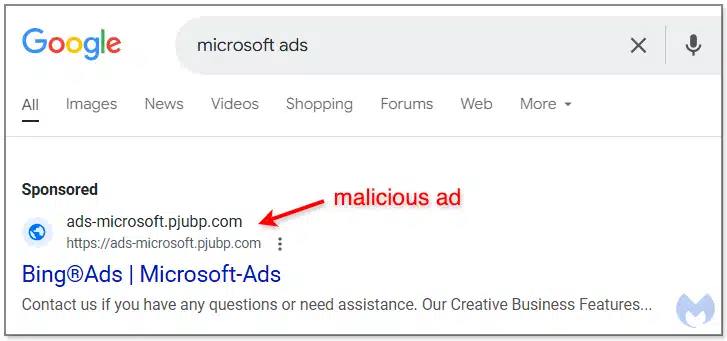
The big picture. Attackers created malicious Google ads mimicking Microsoft Advertising’s official platform. The campaign redirects users through complex networks to steal login information. Researchers discovered potential infrastructure dating back multiple years
How it works. Hackers use a multi-step process to bypass security:
- Create sponsored search results that look like legitimate Microsoft ads.
- Implement cloaking techniques to evade bot detection.
- Use Cloudflare verification to appear more authentic.
- Present a convincing phishing page that mimics Microsoft’s login screen.
Why we care. This threat is significant because it can compromise advertising accounts, potentially leading to financial losses, reputational damage, and disruption of critical marketing operations across digital platforms.
Protect yourself
- Verify URLs carefully before entering credentials.
- Use two-factor authentication wisely.
- Regularly monitor advertising accounts.
- Report suspicious ads.
What’s next? Cybersecurity firms are investigating the broader implications of this phishing infrastructure, which appears to span multiple countries and platforms.
Bottom line. As online advertising becomes more complex, so do the techniques used by cybercriminals to exploit it.
New on Search Engine Land
#Phishing #scam #targets #Microsoft #accounts #Google #Search


Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.